Momentan sehr beliebt
Erkunden
Prime Video: Die Verdeckte Preiserhöhung von Amazon
Am 5. Februar 2024 führt Amazon Prime Video Werbung ein. Kunden in Deutschland haben die Wahl zwischen zusätzlichen Kosten oder der Akzeptanz von Werbung.
APP NEUHEITEN
Prime Video: Die Verdeckte Preiserhöhung von Amazon
Am 5. Februar 2024 führt Amazon Prime Video Werbung ein. Kunden in Deutschland haben die Wahl zwischen zusätzlichen Kosten oder der Akzeptanz von Werbung.
Chinesische VTech Holding übernimmt Gigaset
Die chinesische VTech Holdings Limited übernimmt den deutschen Telefon-Hersteller Gigaset. Sind wenigstens die Arbeitsplätze gesichert? Zweifel sind angebracht.
IN VERBINDUNG BLEIBEN
ELEKTRO AUTOS
Prime Video: Die Verdeckte Preiserhöhung von Amazon
Am 5. Februar 2024 führt Amazon Prime Video Werbung ein. Kunden in Deutschland haben die Wahl zwischen zusätzlichen Kosten oder der Akzeptanz von Werbung.
INTERNET DER DINGE
Dyson 360 Heurist kommt nach Deutschland
Der britische Hersteller Dyson bringt den Nachfolger, des 2016 vorstellen Staubsaugroboters Dyson 360 Eye jetzt auch nach Deutschland. Der Dyson 360 Heurist ist schon länger auf dem Markt, jedoch bisher nicht...
Gigaset stellt Cloud-basierten Anrufschutz fürs Festnetztelefone vor
Mit der Einführung des neuen DECT-Telefons Gigaset CL690A SCB für der deutsche Hersteller aus Bocholt einen neuen Service „Smart Call Block“ für seine IP-Basierten Telefone ein. Smart Call Block ist ein...
Wissenswertes zur eSIM
Wer bisher seinen Mobilfunkanbieter wechselte, wurde bisher meist gefragt, ob er eine passende Mini-, Micro- oder Nano-SIM-Karte für sein Gerät braucht. Das sollte sich mit dem Start der eSIM vor knapp...
Neueste Beiträge
In eigener Sache: moobilux sucht Technikredakteur/in zur Verstärkung
Um die moobilux Besucher auch in Zukunft weiterhin täglich mit den wichtigsten Meldungen rund um Smartphones/Tablets, Apps, Gadgets, eMobility und Startups zu versorgen zu können, suchen wir ab sofort Verstärkung für...
Test: Devolo Home Control
Pünktlich zur kalten Jahreszeit haben wir das Devolo Home Control System für euch an getestet. Wer sich an dieser Stelle fragt was ein Mobile orientiertes Magazin wie moobilux | Connected Mobile...
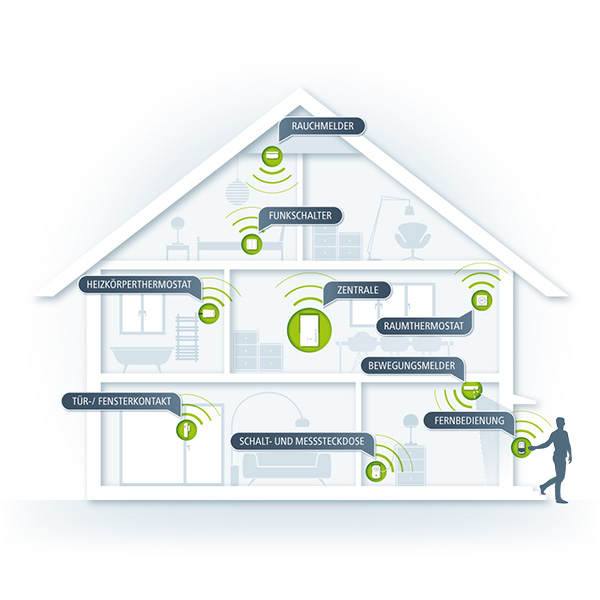
Smart Home das vernetze Zuhause 1/2
Smart Home das vernetze Zuhause 1/2
Das intelligente vernetzte Zuhause, das „Smart Home“ lockt mit Versprechen von mehr Komfort und Lebensqualität. Es soll helfen Energie zu sparen und zugleich einen Zugewinn an...
Prime Video: Die Verdeckte Preiserhöhung von Amazon
Am 5. Februar 2024 führt Amazon Prime Video Werbung ein. Kunden in Deutschland haben die Wahl zwischen zusätzlichen Kosten oder der Akzeptanz von Werbung.
Chinesische VTech Holding übernimmt Gigaset
Die chinesische VTech Holdings Limited übernimmt den deutschen Telefon-Hersteller Gigaset. Sind wenigstens die Arbeitsplätze gesichert? Zweifel sind angebracht.
Apples neue Markt Dominanz
Apple überholt Samsung als führender Smartphone-Hersteller 2023, dominiert den Premium-Markt und setzt neue Trends im Technologie-Wettstreit.
Android: Sicherheitslücke erlaubt Diebstahl aus Passwortmanager
Sicherheitsanalysten warnen vor einer neuen Gefahr für Android-Nutzer, die Passwort-Manager verwenden: Die Experten haben herausgefunden, dass über die Autocomplete-Funktion von Passwörtern sehr leicht Anmeldedaten gestohlen werden können.
Cerabyte: Revolutionäre optische Speichertechnologie verspricht Robustheit & 5.000 Jahre Lebensdauer
Cerabyte, eine inovative Speichertechnologie aus Deutschland, die Daten auf Keramik-beschichteten Glasfolien für 5.000 Jahre sicher bewahrt.
Honor Magic 6 Pro mehr als per Notrufe per Satellit
Honor Magic6 Pro setzt auf Satellitenkommunikation, bietet Textnachrichten und Anrufe ohne Netz. Honor-CEO bestätigt Technologie.
5G-Erweiterung im National Roaming: Telefónica sieht potenzielle Umsatzsteigerung mit 1&1
Telefónica profitiert kurzzeitig von erweitertem National Roaming-Vertrag mit 1&1, umfasst 2G/4G/5G-Netze und stärkt kurzfristig Einnahmen.
Stiftung Warentest: Den sehr guten Cloud-Dienst gibt es nicht
Die Stiftung Warentest hat neun Clouddienste genauer untersucht. Einer bekam die Note „mangelhaft“ und auch Apple schnitt nicht gut ab.
Magic 6 Pro: Neues Honor-Flaggschiff mit frischen Ideen
Honor Magic 6 Pro: Neues Flaggschiff mit Snapdragon 8 Gen 3, eigenem LLM und Augentracking 'Magic Capsule' für 2024.
DEF CON zeigt iPhone-Bluetooth-Schwachstelle
Auf der DEF CON in Las Vegas hat ein Hacker namens Jae Bochs gezeigt, wie eine Schwachstelle im iPhone-Bluetooth ausgenutzt werden kann.